Setup - AWS & AWS GovCloud¶
Note
Looking for Azure setup instructions? To get started with Fugue on Microsoft Azure, see Setup - Azure & Azure Government.
Looking for Google setup instructions? To get started with Fugue on Google Cloud Platform, see Setup - Google Cloud.
Looking for Repository setup instructions? To get started with Fugue on Repository, see Setup - Repository.
Ready to create a Fugue environment? An environment contains resources from a single AWS account, Azure subscription, Google project, or code repository – in this case, Amazon Web Services (AWS). Fugue surveys the resource configuration in an environment and reports whether the infrastructure is compliant with a particular compliance standard.
Tip
In a hurry? For an even quicker setup guide, see Get Started in 5 Minutes.
To learn more about the basics of using Fugue, see Fugue 101.
Sign Up for Fugue¶
Before you can create an environment, you’ll need to sign up for a free account with Fugue. (You’ll start off with a free Enterprise trial, which gives you access to all of Fugue’s features; after 30 days, you’ll be transitioned to the free-forever Developer plan if you choose not to upgrade.)
Once you’re all signed up and logged in, select the Define New Environment button:
Step 1: Setup (Name, Provider)¶
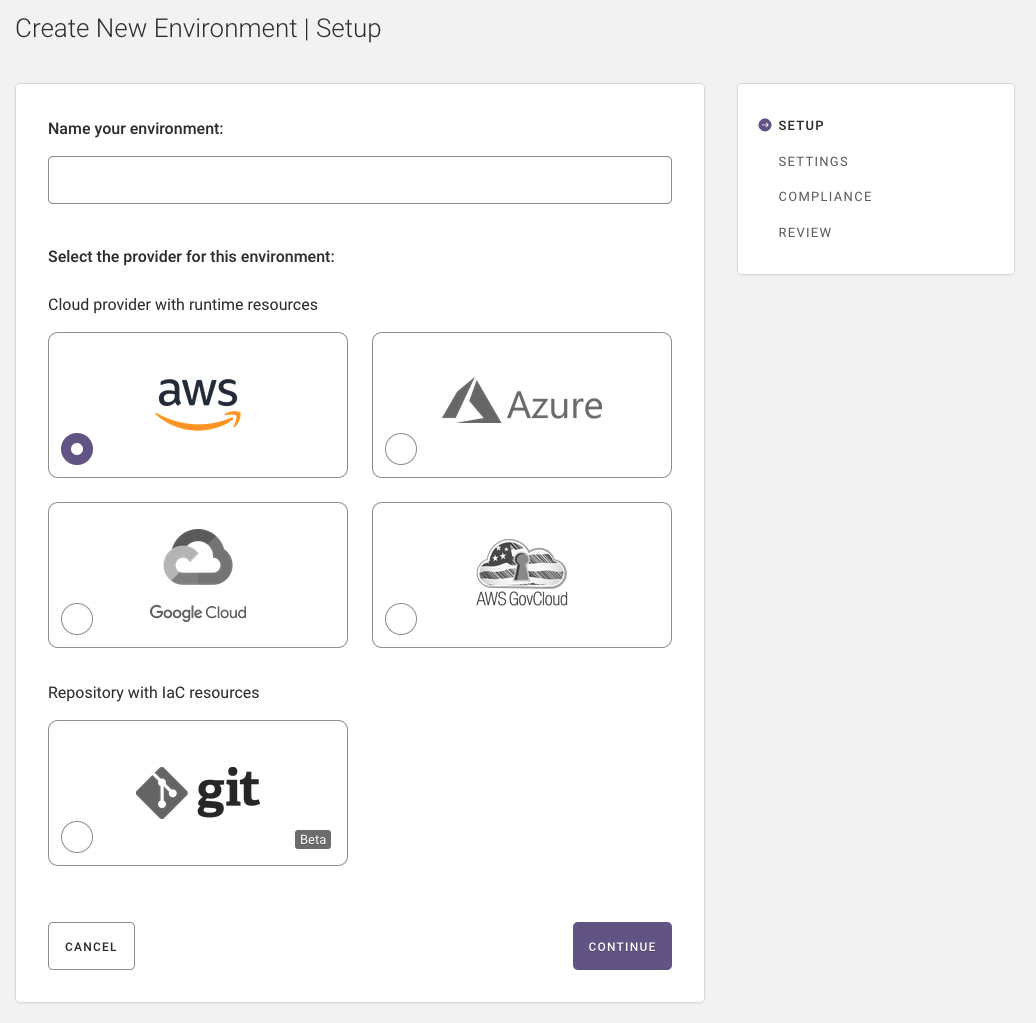
In the first step of creating an environment, you name it and specify your provider – cloud or repository.
Name your environment.
Select the cloud provider (AWS is selected by default).
Select Continue.
Step 2: Settings (Region & Resources, IAM Role)¶
Note
If at any point you want to change something, you can select “Back” at the bottom of the page to return to the previous step, or “Edit” in the sidebar next to the desired step to return to that step.
Step 2 has two parts, which we’ll detail next:
2a. Select one or more regions and resource types to scan.
2b. Create an Identity & Access Management (IAM) role so Fugue can scan your resource configuration.
Step 2a: Select Region(s) and Resource Types¶
Select One or More Regions¶
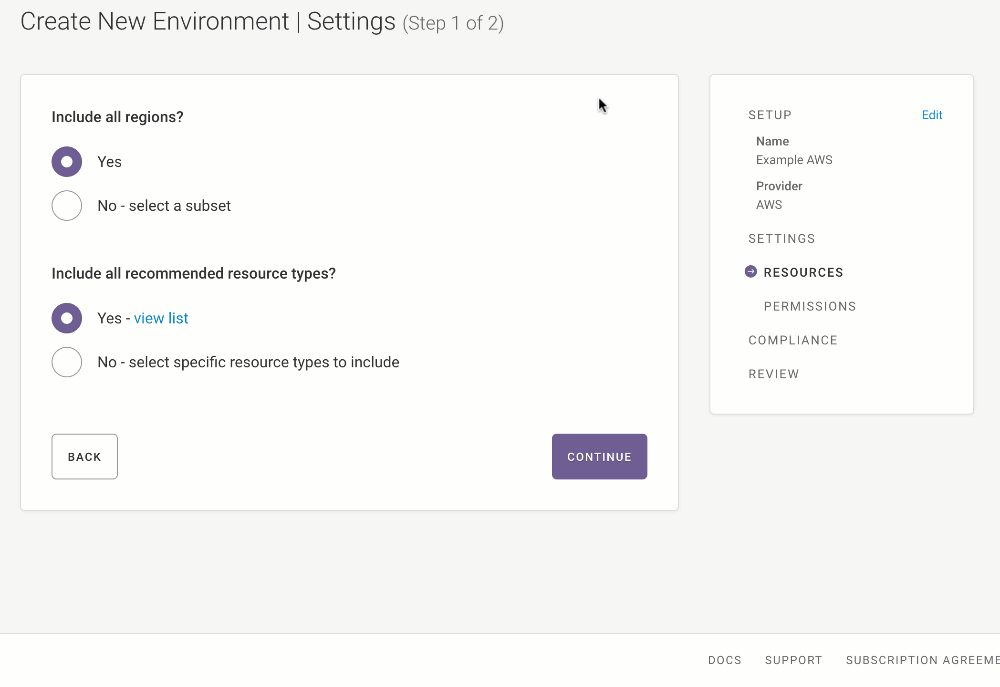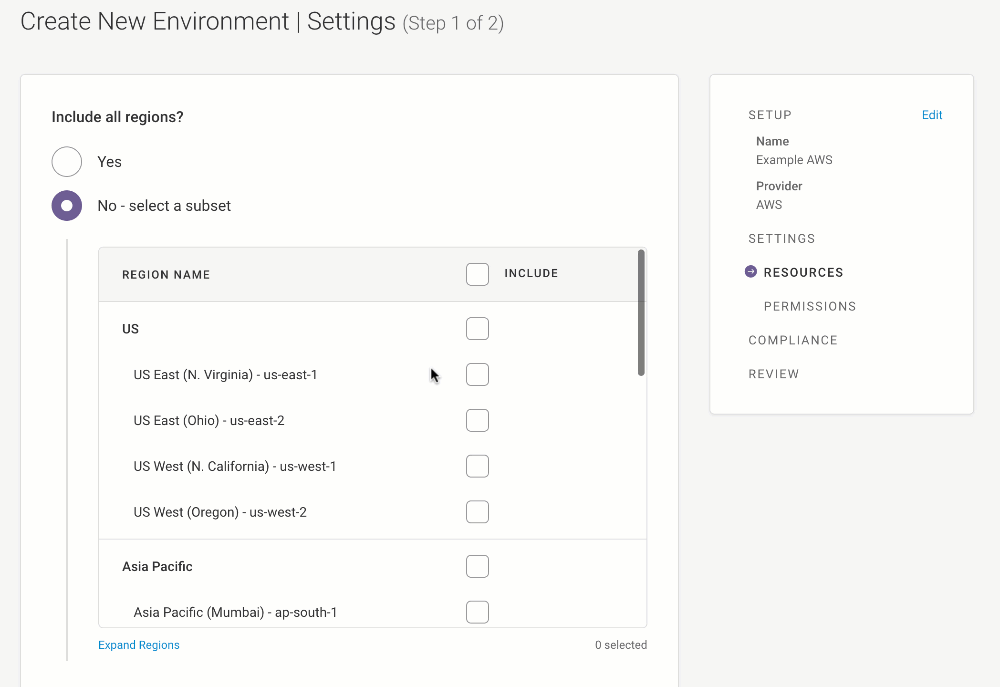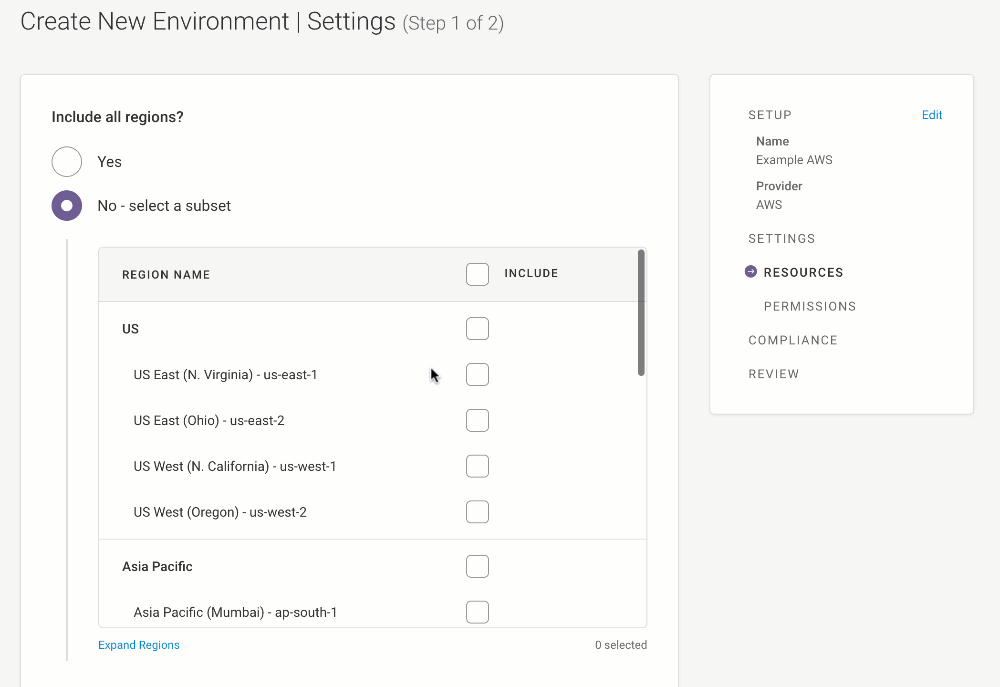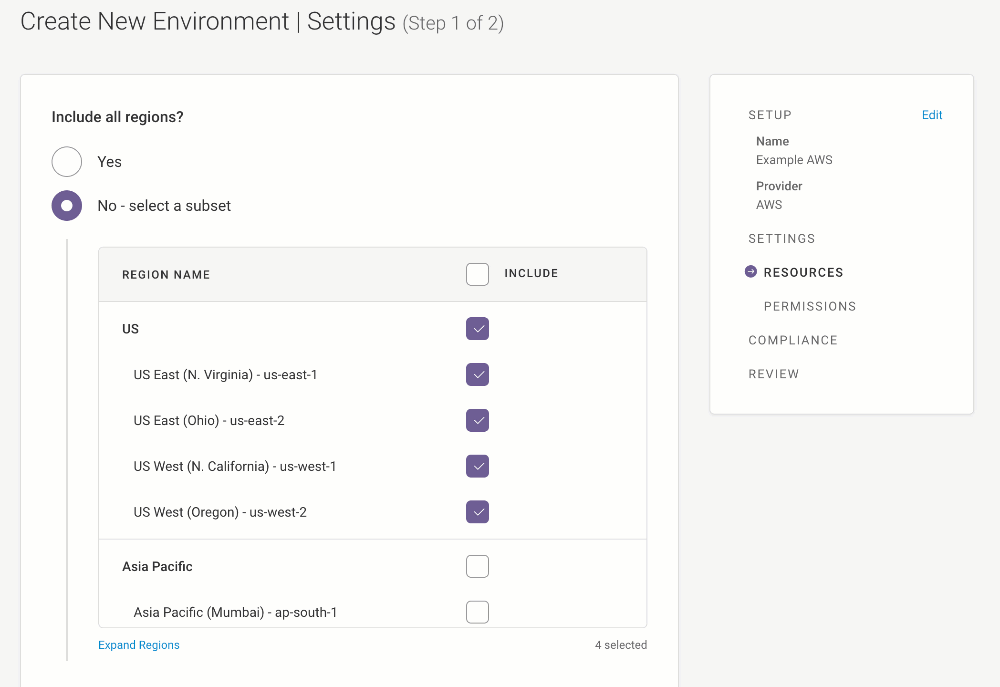
If you’d like Fugue to scan the infrastructure configuration of all regions in your AWS account, select Yes for “Include all regions?”
If you’d prefer to select the region(s) Fugue should scan, you can pick “No - select a subset” and check the box for the desired region(s).
(For a list of supported AWS regions, see the FAQ.)
Note
Some environments support region updates via the API. This only applies to environments that use the regions body parameter, not region. You can check this parameter through the API. See the API User Guide for details.
Select Resources¶
Warning
If you change resource types later, you must also update Fugue’s IAM role or scans will fail. For instructions, see How To: Update the Fugue IAM Role.
In order to get the most out of Fugue, you can opt to scan a Fugue-recommended set of resource types when creating an environment. We’ve chosen these resources for the Fugue Recommended Resource Types list because of their high impact on security, and they include security groups, IAM roles, S3 buckets, and more.
For details, see the lists of recommended AWS resources and AWS GovCloud resources, or view the list of all supported resources.
If you’d like to select the recommended resource types, ensure “Yes” is selected. You can see which resources are included by clicking view list.
If you’d prefer to select the resource types yourself, click No - select specific resource types to include and choose the desired resources. You can search for a resource type by name.
AWS GovCloud Resources¶
If you’ve selected a GovCloud region, the list of available resources shows only the resources that are supported in GovCloud. To view the list of resources Fugue supports in AWS standard regions vs. in AWS GovCloud, see Service Coverage - AWS & AWS GovCloud.
Note that Fugue scans and enforces AWS GovCloud environments but is itself hosted in an AWS standard region. It uses a cross-account role that exists in a Fugue-owned GovCloud account.
Step 2b: Create IAM Role¶
Warning
If you change resource types later, you must also update Fugue’s IAM role or scans will fail. For instructions, see How To: Update the Fugue IAM Role.
To scan your AWS account, Fugue uses a strictly permissioned IAM role based on the resource types selected in the previous step. You can see a list of all possible Fugue permissions here.
There are three ways to create the IAM role:
Launch CloudFormation stack (Default)
Run AWS CLI command (Advanced)
Create IAM Role Via CloudFormation Stack (Default)¶
Tip
If you’d like a little more detail, see our tutorial How To: Create a Fugue IAM Role.
Note
Fugue automatically attaches the read-only AWS-managed SecurityAudit to the created role.
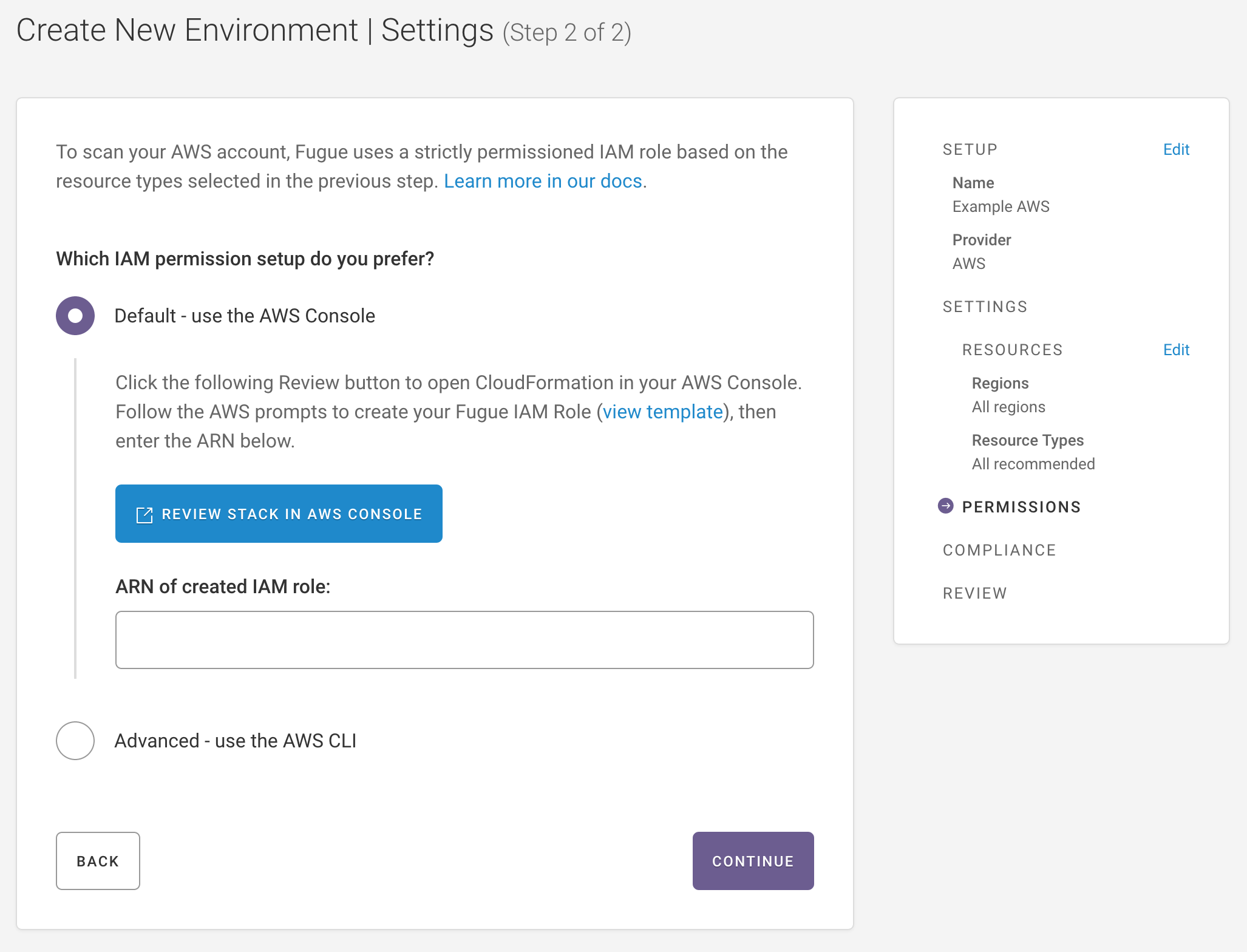
Ensure Default - use the AWS Console is selected.
If you’d like to view the IAM role or policy permissions in the CloudFormation template before continuing, select view template.
Select Review Stack in AWS Console.
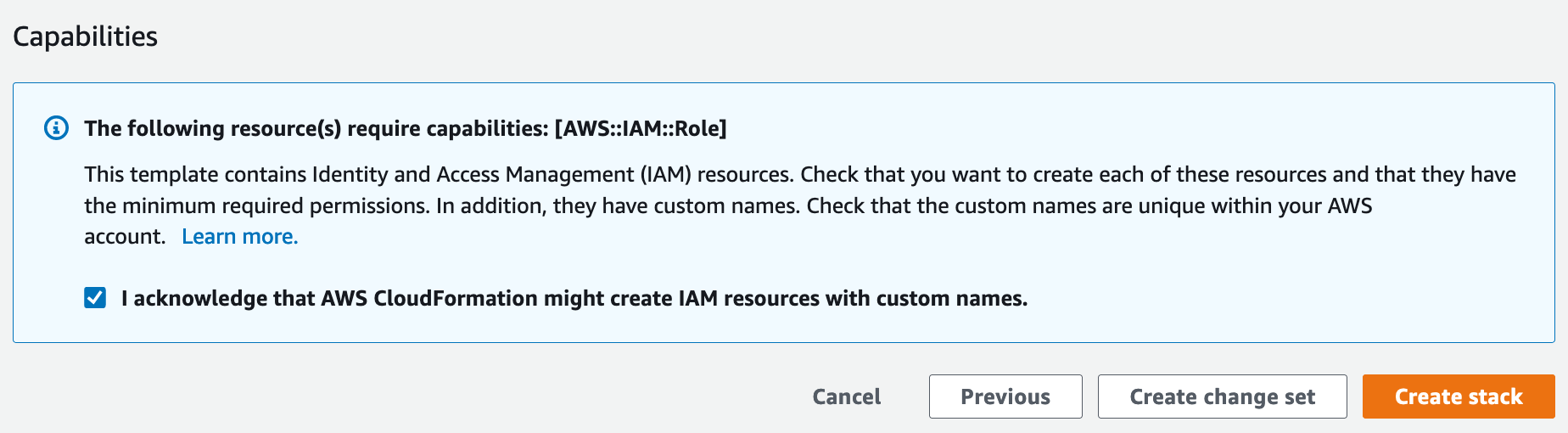
On the AWS CloudFormation “Create stack” page, follow the prompts (defaults are fine) by clicking Next until you reach a page requesting acknowledgement for creating the required IAM resources.
Check the box to acknowledge that the IAM resources may have custom names.
Select Create stack to go to the CloudFormation stacks page while AWS creates the IAM role and policy. (It typically takes less than a minute for AWS to finish creating the resources.)
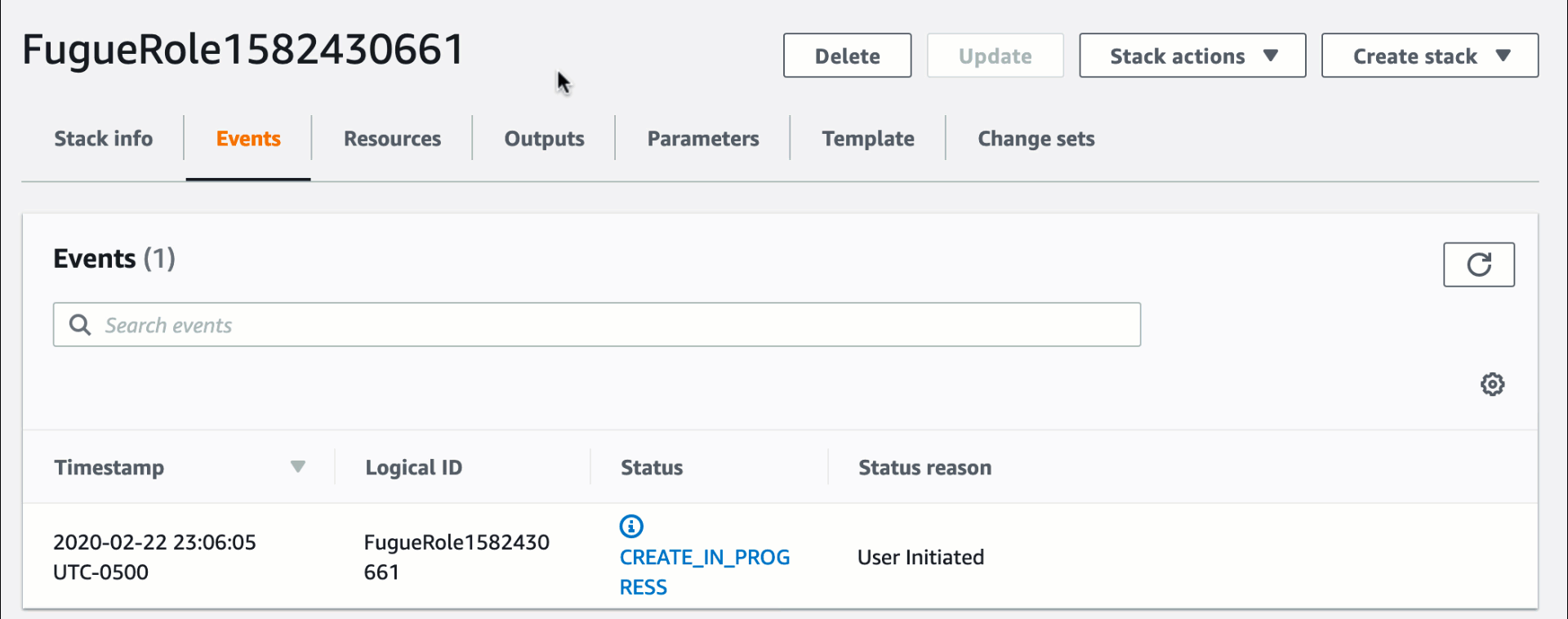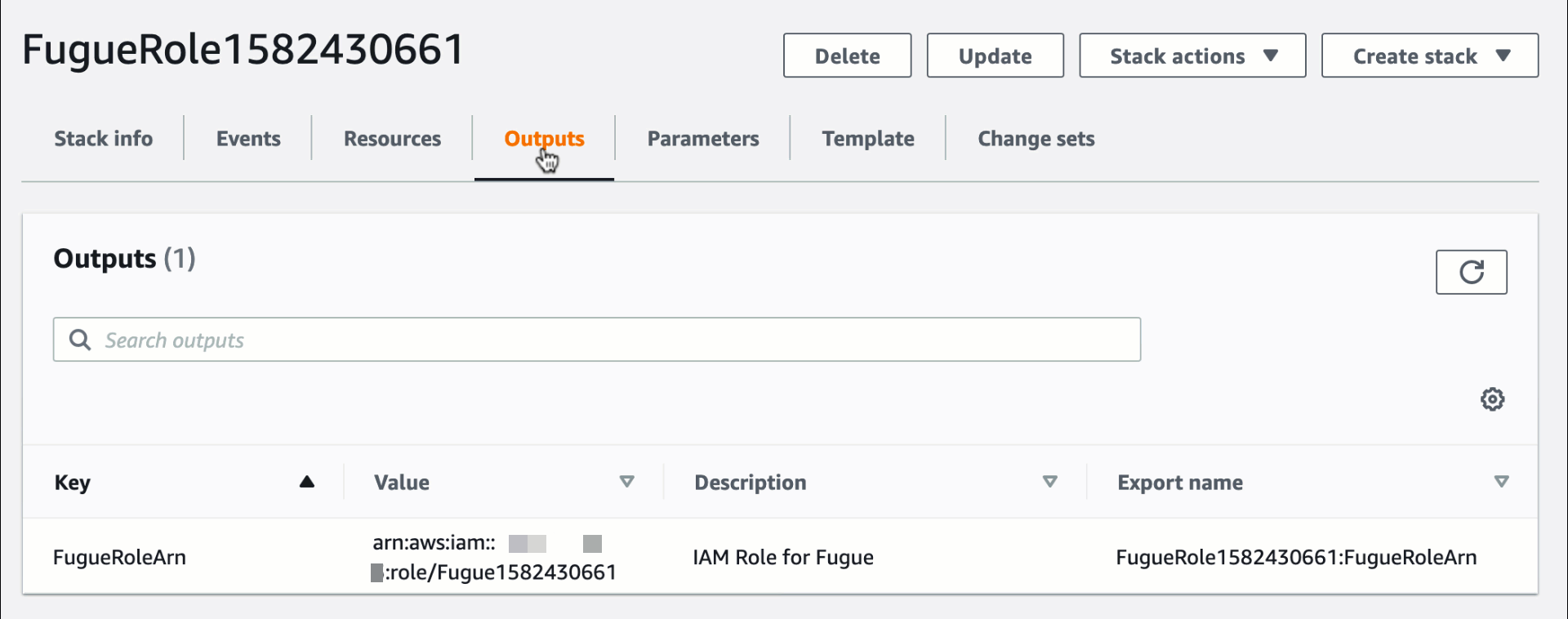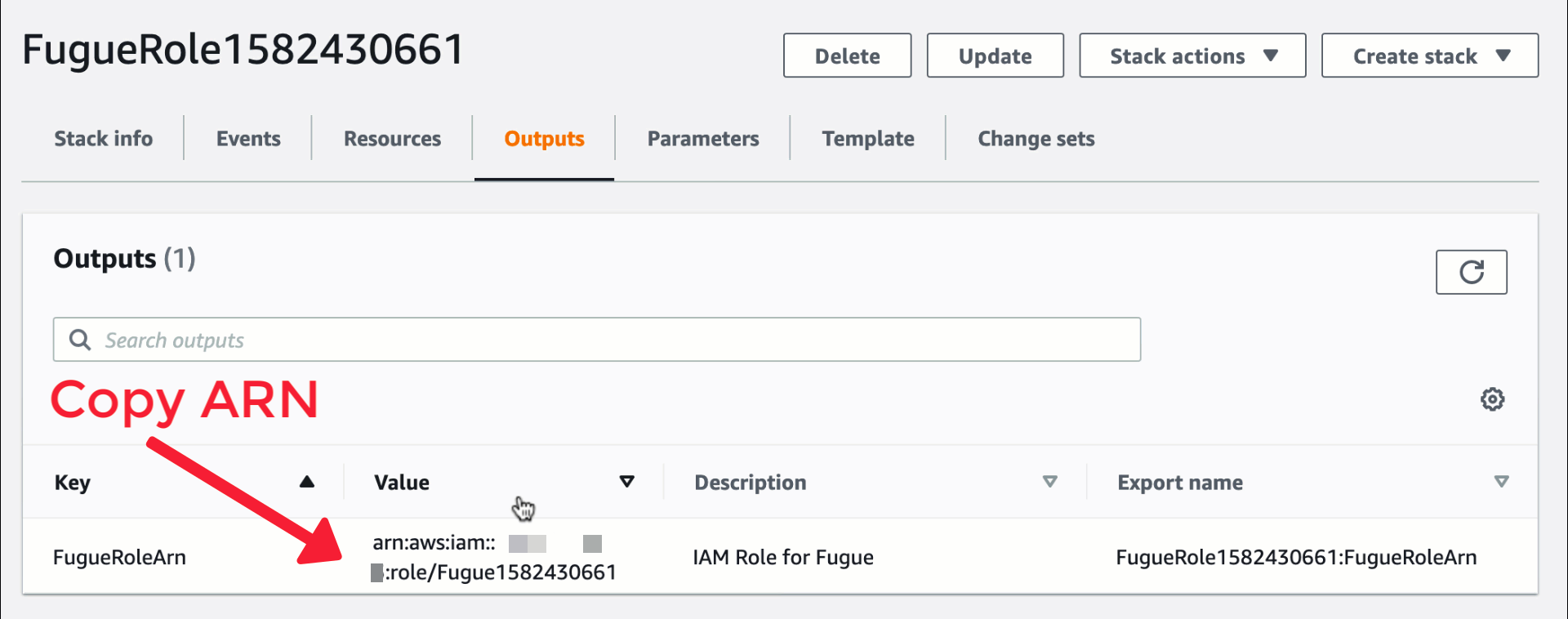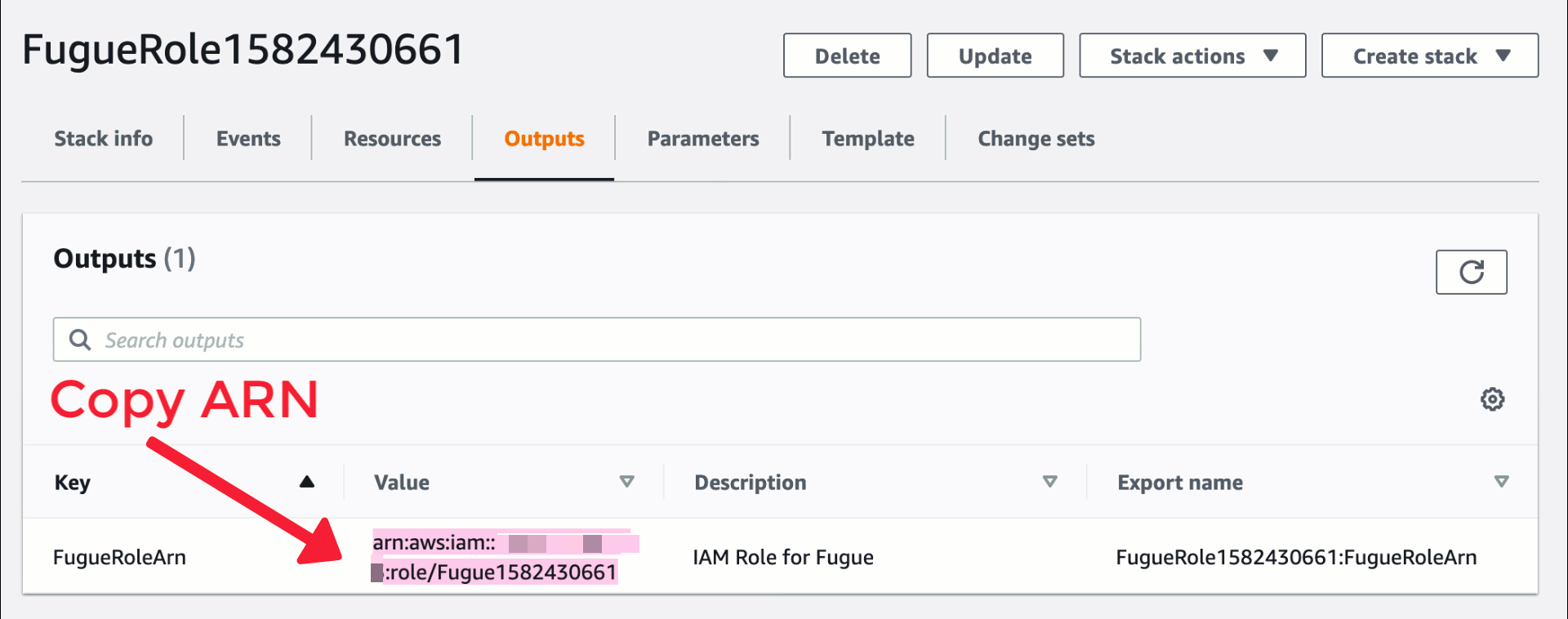
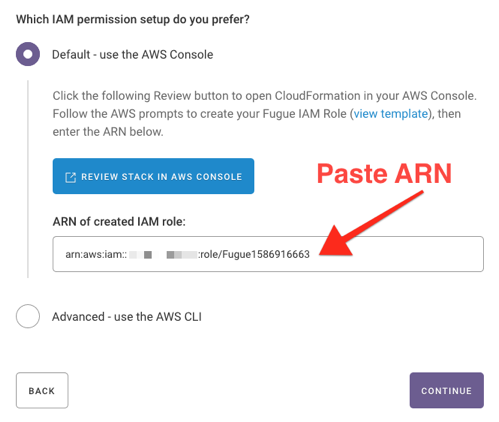
7. Once the stack is created, click on the Outputs tab and copy the role ARN.
8. Paste the ARN into the ARN of created IAM role field on the Fugue environment setup page.
The next step is to choose compliance standards, so jump ahead to continue setup.
Note
If you create or edit a CloudFormation stack through CloudFormation Designer or by uploading a CloudFormation template through the AWS Console or CLI, AWS stores the template files in an S3 bucket created for the purpose of holding all templates in a given region.
Create IAM Role Via AWS CLI (Advanced)¶
Note
Fugue automatically attaches the read-only AWS-managed SecurityAudit to the created role.
If you’re comfortable with the AWS CLI, you can run a command to create the Fugue IAM role.
Select Advanced - use the AWS CLI.
If you’d like to view the IAM role or policy permissions in the CloudFormation template before continuing, select view template.
Copy the AWS CLI command, which launches a CloudFormation stack to create the role and policy.
When the resources have been created, the command returns the ARN of the role. Copy the ARN.
Paste the ARN into the ARN of created IAM role field on the Fugue environment setup page.

The next step is to choose compliance standards, so jump ahead to continue setup.
Step 3: Compliance¶
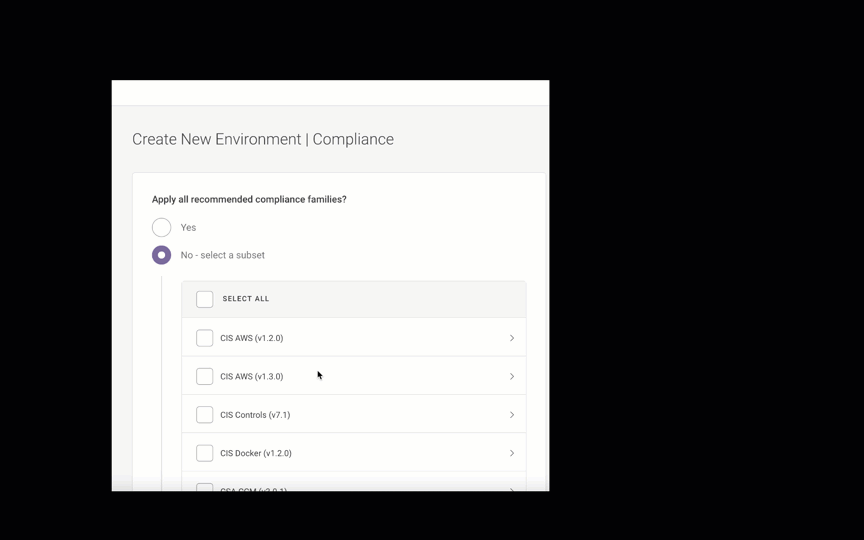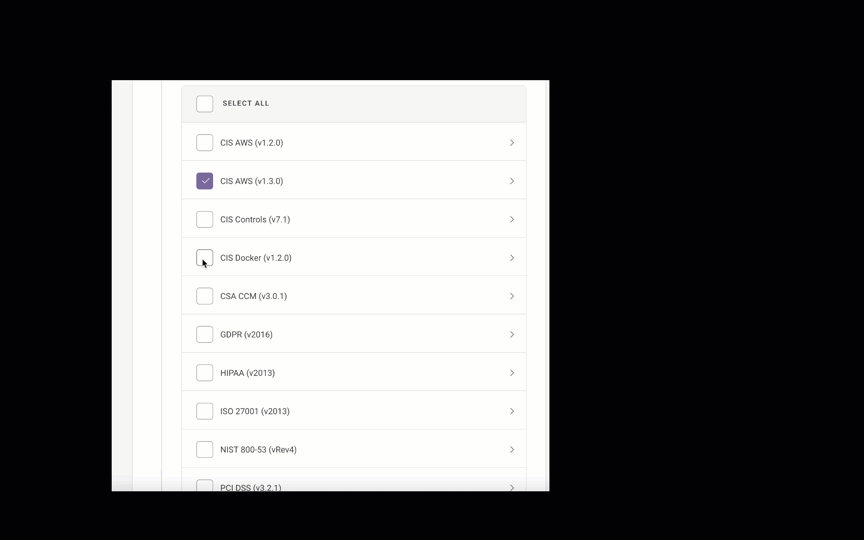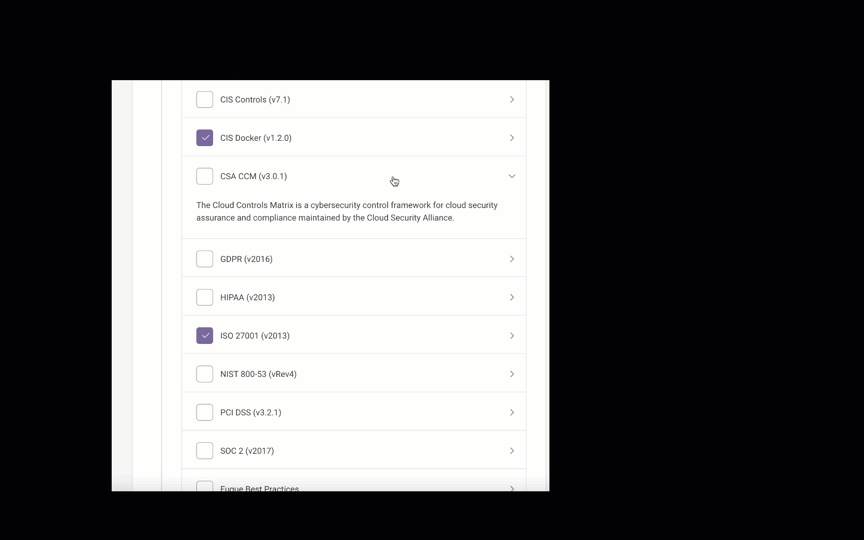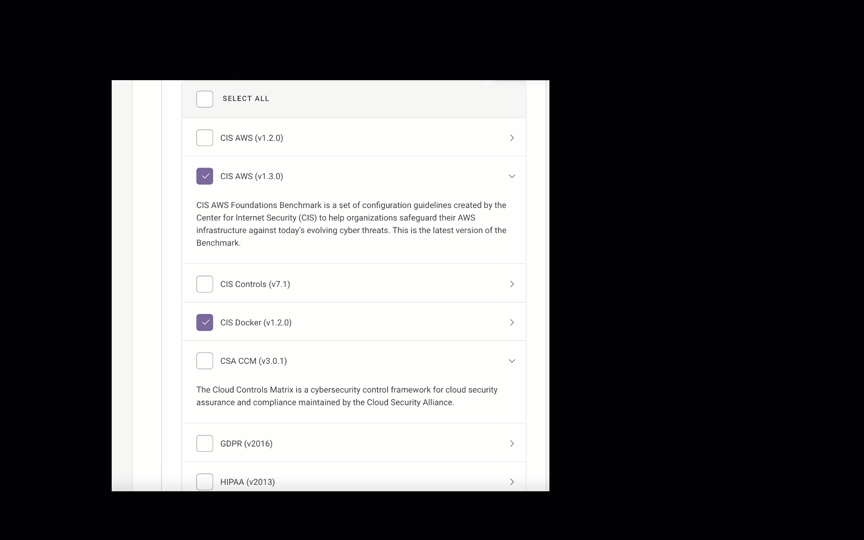
If you’d like Fugue to evaluate your infrastructure configuration for all compliance standards, ensure “Yes” is selected.
If you’d prefer to select the compliance families yourself, click No - select a subset.
Fugue supports the following compliance families for AWS environments:
AWS Well-Architected (v2020-07-02)
CIS AWS (v1.2.0)
CIS AWS (v1.3.0)
CIS AWS (v1.4.0)
CIS Controls (v7.1)
CIS Docker (v1.2.0)
CSA CCM (v3.0.1)
Fugue Best Practices
GDPR (v2016)
HIPAA (v2013)
ISO 27001 (v2013)
NIST 800-53 (vRev4)
PCI DSS (v3.2.1)
SOC 2 (v2017)
AWS GovCloud Compliance Standards¶
AWS and AWS GovCloud environments offer the same list of compliance standards. However, AWS GovCloud regions only support a subset of the services available in standard regions, so GovCloud regions support a subset of available compliance controls. For controls that require service coverage that is not supported in GovCloud, the compliance state is listed as Missing Data. To view the list of resources Fugue supports in AWS GovCloud, see Service Coverage - AWS & AWS GovCloud.

Step 4: Review¶
Review the details for your environment, including environment name, region(s), AWS IAM role ARN, resource types, and compliance standards.
If anything needs to be changed, click Edit next to the appropriate step, as highlighted below.
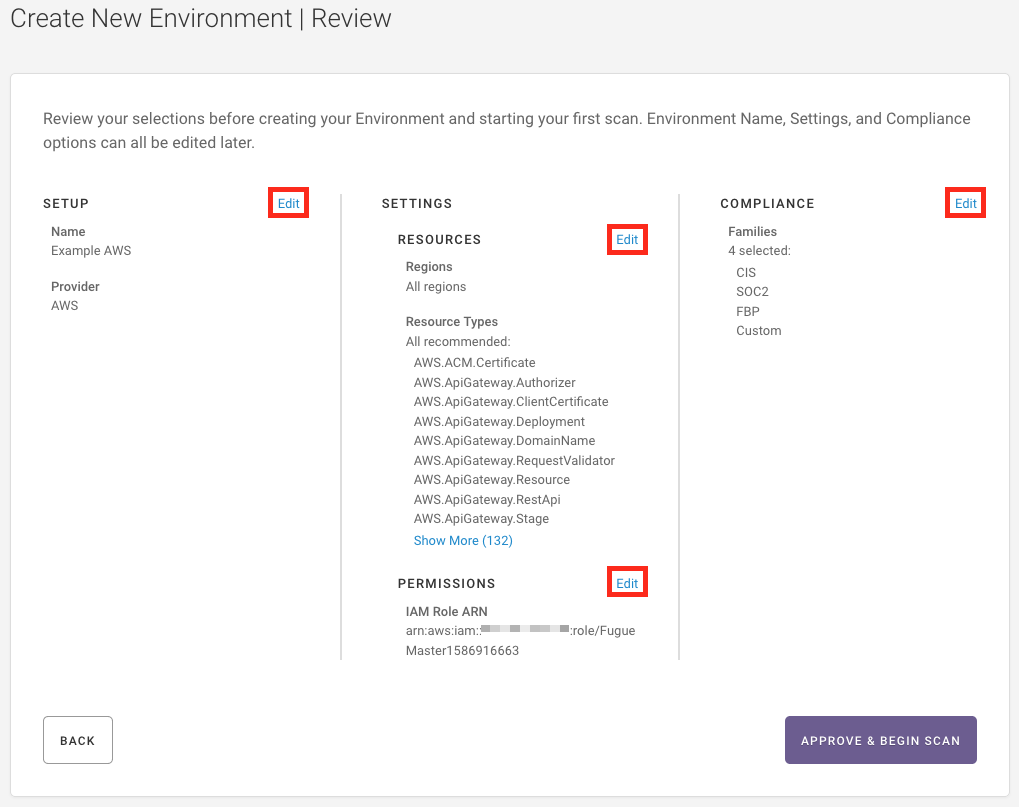
3. If everything looks good, select the Approve and Begin Scan button. Fugue will create your environment and start to scan your infrastructure.
When the scan is complete, Fugue brings you to your environment’s dashboard, where you can see your compliance state.
Congratulations! You’ve just created an AWS or AWS GovCloud environment with Fugue.
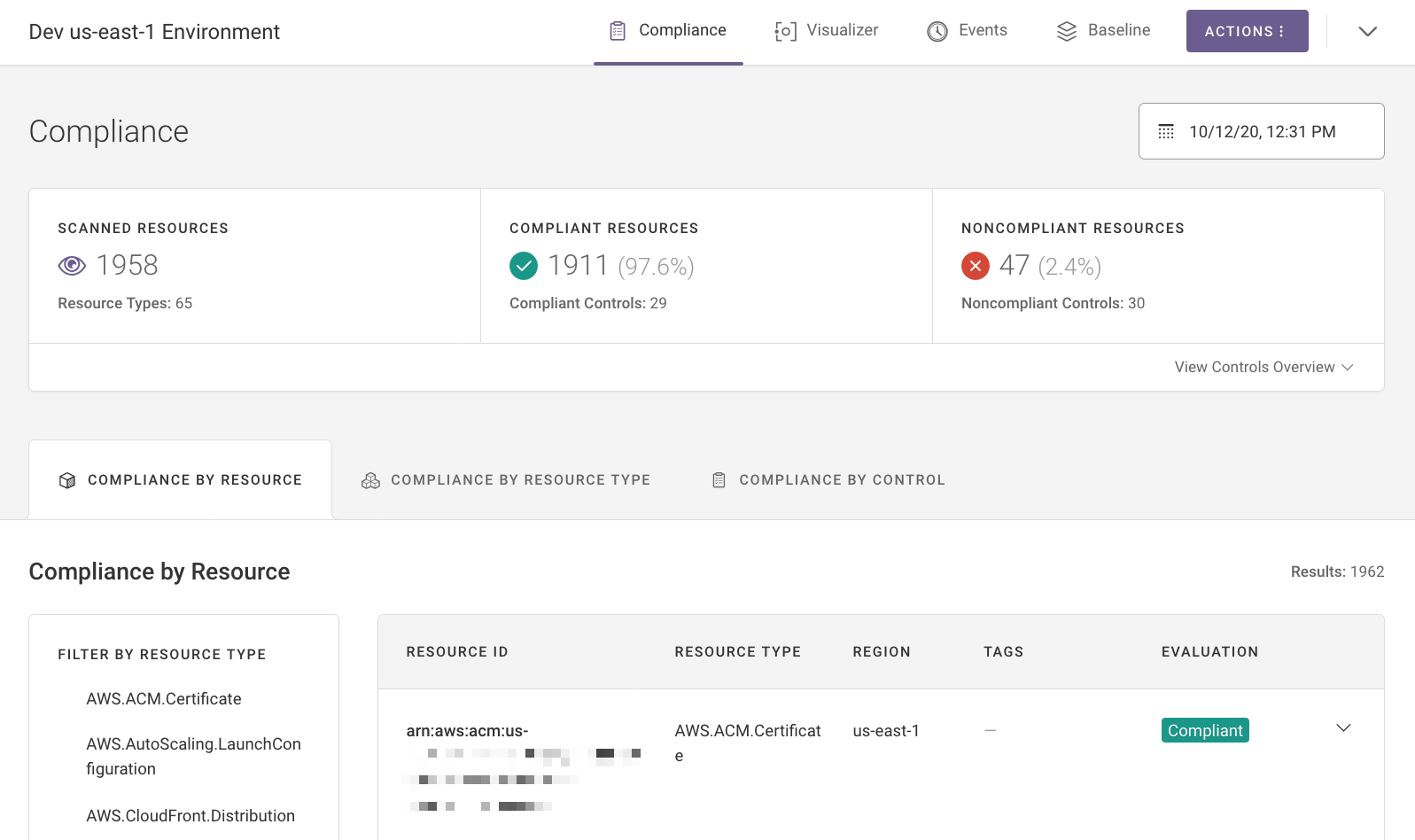
What’s Next?¶
Fugue will continue to scan the resource configuration in your environment at regular intervals (and on demand). This is how Fugue detects compliance violations in your infrastructure.
Now that you’ve created an environment, learn how to configure it further in Environment Configuration. If you’d like to learn more about checking compliance state, see Compliance. Or, check out the visualizer for an interactive diagram of your cloud infrastructure.