FAQ¶
General¶
How do I contact support?¶
To contact Fugue support, reach out to support@fugue.co. You can also check out Support for self-service help.
Where can I sign up for Fugue?¶
How can I get started with my first environment?¶
How do I change my Fugue user password?¶
Note
These instructions does not apply to organizations that have enabled single sign-on, except for the organization account owner. Users in an SSO-enabled organization do not use a Fugue username and password to log in.
To change your Fugue user password, follow these steps:
Select the “Don’t remember your password?” link on the login page or access the Forgot Password page directly.
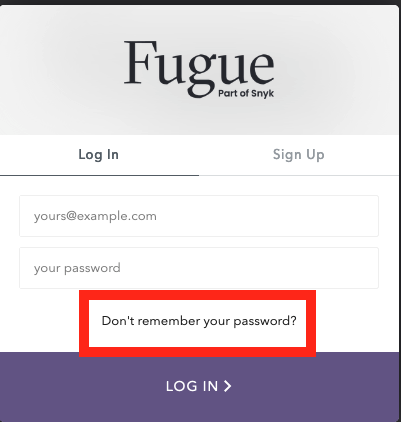
2. Enter your email address in the “Forgot Your Password?” form.
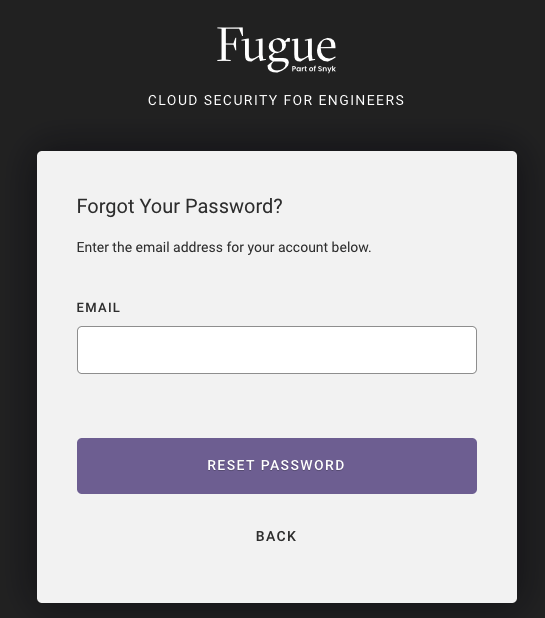
3. After you submit the form, you’ll see a message that the password reset email was sent. Check your inbox for an email from Fugue and click the “Reset Password” button in it.
4. Next, enter and confirm your new password in the “Reset Password” form. Your password must be at least 8 characters long.
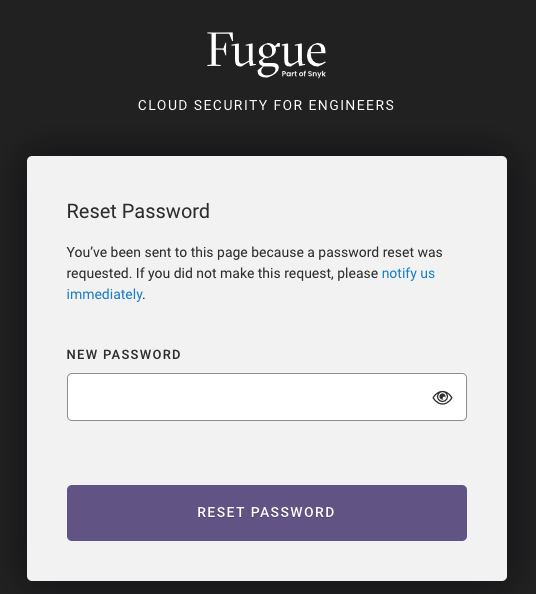
5. Finally, after you submit the form, you’ll see a message that your password has successfully been reset, and you can log into your account using the new password.
What browsers are supported?¶
Fugue supports the following browsers:
Chrome
Firefox
Microsoft Edge
Opera
Safari
What are Fugue’s email addresses that should be whitelisted?¶
Depending on your email setup, emails sent from Fugue may go into your spam folder. To avoid each user from having to manually report the email as not junk, you can implement a whitelist of the domains from which Fugue sends notifications:
Plans¶
What plans are offered?¶
Fugue is available with three paid plans and a Developer (free) plan. All Fugue accounts start with a free 30-day trial of Enterprise. For more information, see Fugue Plans.
What’s the difference between Enterprise Trial, Paid Plans, and the Developer Plan?¶
All new users will have access to our free 30-day Enterprise trial, during which you will have access to all of our features. After the conclusion of the trial, you have the option to purchase a paid plan or your account will be transitioned to our free plan, Fugue Developer. For a side-by-side comparison, see Plan Comparison.
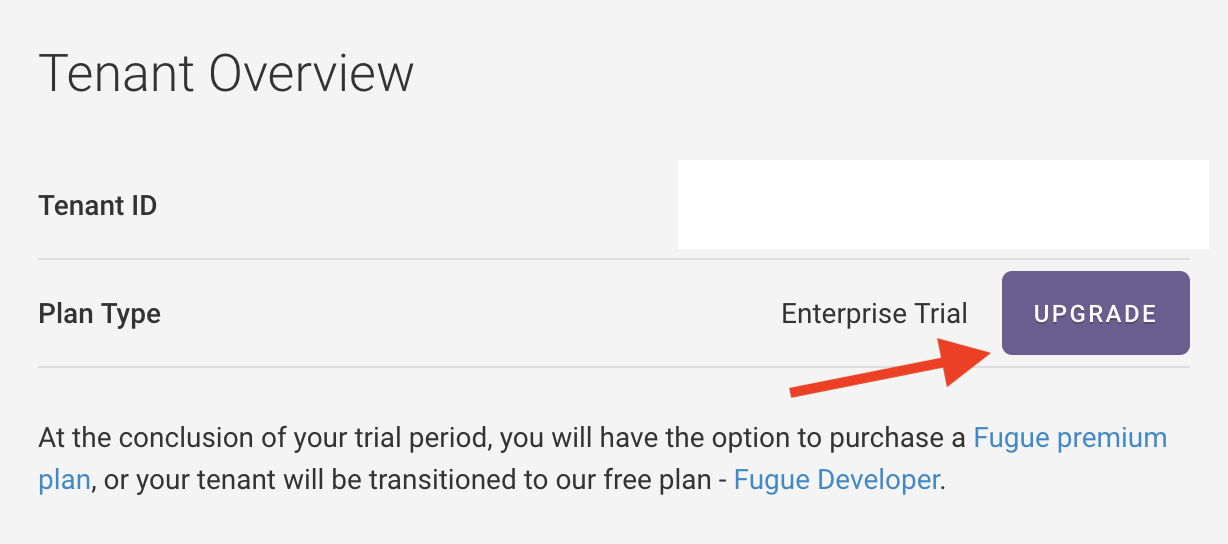
How do I upgrade my Fugue tenant?¶
To upgrade to the a paid plan from the Enterprise trial or Developer plan, contact sales@fugue.co, or select the “Upgrade” button next to your plan type on the Tenant Overview page:
How do I find out what my plan is?¶
The Tenant Overview page lists your current plan.
How is scanning limited in Fugue Developer?¶
In Fugue Developer, on-demand scans are limited to 10 per rolling 24-hour period. After you hit the on-demand scan limit, a new scan is allotted every 2.4 hours. To scan on demand, use the Fugue UI or API.
There is a 24-hour minimum interval for scheduled (aka automatic) scans, so scans are limited to once per day. You may set the interval to be longer.
Scheduled scans do not count toward the on-demand scan limit.
How much does it cost?¶
Fugue Developer is free forever. See Plans and Pricing for paid plans pricing.
Where can I find more information?¶
See the FAQ in Plans and Pricing.
Environments¶
How many environments can Fugue store?¶
There is currently no specific limit on the number of environments you can create with paid plans.
Does Fugue support AWS GovCloud?¶
Yes. All activities that are supported in standard AWS regions are supported in AWS GovCloud regions. To learn more about setting up a GovCloud environment, see Setup - AWS & AWS GovCloud.
To see a list of services and resources supported in AWS GovCloud, see Service Coverage - AWS & AWS GovCloud.
For details on the differences between standard AWS regions and the GovCloud AWS regions, refer to Amazon’s documentation about service-specific differences and general differences.
What AWS and AWS GovCloud regions does Fugue support?¶
Fugue supports the following regions:
US East (N. Virginia) - us-east-1
US East (Ohio) - us-east-2
US West (N. California) - us-west-1
US West (Oregon) - us-west-2
Asia Pacific (Mumbai) - ap-south-1
Asia Pacific (Seoul) - ap-northeast-2
Asia Pacific (Singapore) - ap-southeast-1
Asia Pacific (Sydney) - ap-southeast-2
Asia Pacific (Tokyo) - ap-northeast-1
Canada (Central) - ca-central-1
EU (Frankfurt) - eu-central-1
EU (Ireland) - eu-west-1
EU (London) - eu-west-2
EU (Paris) - eu-west-3
EU (Milan) - eu-south-1 (beta)
EU (Stockholm) - eu-north-1
Middle East (Bahrain) - me-south-1 (beta)
South America (São Paulo) - sa-east-1
AWS GovCloud (US East) - us-gov-east-1
AWS GovCloud (US West) - us-gov-west-1
Environments can include a single region or any combination of regions, including all.
How can I change my AWS environment’s region(s)?¶
AWS environments support region updates via the API. This only applies to environments that use the regions body parameter, not region. You can check this parameter through the API. See the API User Guide for details.
Does Fugue support Microsoft Azure and/or Azure Government?¶
Yes, Fugue supports Microsoft Azure and Azure Government. You can use Fugue to scan resource groups in your Azure subscription for compliance assessment and drift detection.
Follow the same steps to create and configure Azure Government environments as you would Azure environments. When selecting a provider, such as during custom rule creation or when using the API, always select Azure.
For general information about using Fugue with Azure, including setup instructions, see Setup - Azure & Azure Government. For service coverage, see Service Coverage - Azure & Azure Government. If you have any other questions about Fugue and Azure, reach out to support@fugue.co.
Does Fugue support Google Cloud?¶
Yes, Fugue supports Google Cloud. You can use Fugue to scan Google Cloud projects for compliance assessment and drift detection. For service coverage, see Service Coverage - Google Cloud. If you have other questions about Fugue and Google Cloud, reach out to support@fugue.co.
Note
Fugue does not support scanning of organizational level resources for Google.
Does Fugue support infrastructure as code?¶
Yes, Fugue repository environments integrate with Regula to scan infrastructure as code files for cloud resource configurations.
How can I quickly create multiple environments?¶
You can automate creation of Fugue environments using our utility scripts:
Create Fugue environments for a list of accounts and regions
Create Fugue environments for a list of accounts and regions extracted from AWS Organizations
For other useful scripts, see our GitHub repo common-utility-scripts.
Scanning¶
How can I trigger a scan?¶
You can trigger a scan using the UI or API. For instructions, see Triggering a Scan.
Where do I view my scan results?¶
Once your environment is established, your scan results will display on the environment dashboard.
How can I change the resources that Fugue scans in my AWS Commercial or GovCloud environment?¶
Changing the AWS resources Fugue scans is a two-step process:
Select
 Edit Environment from the Actions drop-down in the top right of the page and select/deselect resources you want to include or exclude from scanning, then click “Save changes.” See Service Coverage - AWS & AWS GovCloud for a list of supported resources.
Edit Environment from the Actions drop-down in the top right of the page and select/deselect resources you want to include or exclude from scanning, then click “Save changes.” See Service Coverage - AWS & AWS GovCloud for a list of supported resources.Update the IAM policy for the Fugue role. For instructions, see How To: Update the Fugue IAM Role.
The next scan includes the updated resource types. You can manually trigger a scan via the UI or API.
Warning
After updating the permissions in Fugue, you must update its IAM role in AWS or scans will fail. For instructions, see How To: Update the Fugue IAM Role. You can also reach out to support@fugue.co.
How can I change the resource groups Fugue scans in my Azure environment?¶
To add or remove resource groups after the environment has been created, you must use the Fugue API. See How To: Add or Remove Azure Resource Groups for details.
What does the red “Something went wrong” banner mean?¶
When viewing an environment, if you see a red banner with the text “Something went wrong during the most recent attempt to scan your environment,” that means there was a scan failure. If you click the “View details” link, you’ll see a “Last Scan Failed” message with an error message and a link to contact support:
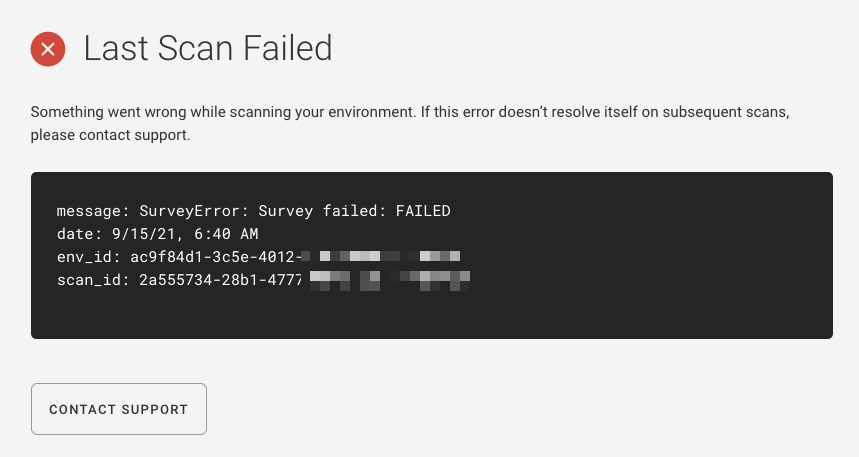
Click the “Contact Support” button to create an email to support@fugue.co. The email will be auto-populated with the error message, and you can add any details you’d like before sending it.
What does the orange “Incomplete Scan Results” banner mean?¶
When viewing an environment, if you see an orange banner with text like “Incomplete Scan Results on 9/14/21, 2:56 PM – Unable to access all selected resources,” it means Fugue was most likely unable to scan all of your resources due to permissions issues, throttling, or other reasons. Fugue may have been able to scan some (or all) resources. If you select the “View details” link, you’ll see an “Incomplete Scan Results” message with an error message and a link to contact support.
For instance, you might see an error like this if Fugue does not have permission to scan all of your selected AWS resources:
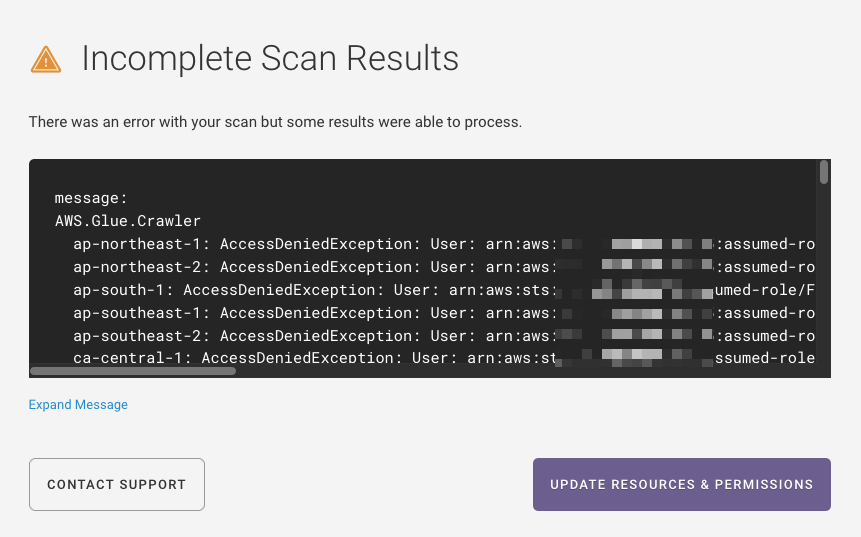
In this situation, you can edit your existing AWS IAM role to add the required permissions. Select the “Update Resources & Permissions” button to edit your environment settings and follow the steps in How To: Update the Fugue IAM Role to update your IAM role and give Fugue the permissions required to scan all your selected resources.
You can also click the “Contact Support” button to create an email to support@fugue.co. The email will be auto-populated with the error message, and you can add any details you’d like before sending it.
Can I scan ElastiCache clusters within a replication group?¶
When ElastiCache.Cluster resources belong to an ElastiCache.ReplicationGroup, the clusters themselves are not scanned but the replication group is. The replication group manages the clusters and contains all of the relevant settings, so there is no need to scan
the clusters individually.
In contrast, ElastiCache clusters that do not belong to a replication group are scanned individually.
Compliance¶
Which compliance families are supported?¶
Currently, Fugue supports the following compliance families:
AWS Well-Architected (v2020-07-02)
CIS AWS (v1.2.0)
CIS AWS (v1.3.0)
CIS AWS (v1.4.0)
CIS Azure (v1.1.0)
CIS Azure (v1.3.0)
CIS Controls (v7.1)
CIS Docker Benchmark (v1.2.0)
CIS Google (v1.1.0)
CIS Google (v1.2.0)
CIS Kubernetes (v1.6.1) (limited beta: Only supported for Repository environments)
CSA CCM (v3.0.1)
FBP
GDPR (v2016)
HIPAA (v2013)
ISO 27001 (v2013)
NIST 800-53 (vRev4)
PCI DSS (v3.2.1)
SOC 2 (v2017)
Can I change the compliance families Fugue uses to evaluate my infrastructure?¶
Yes. You can change them at any time by selecting the Actions button on the top right of an environment page, selecting ![]() Edit Environment from the drop-down menu, and accessing the Compliance tab. Simply check or uncheck the desired compliance family boxes and select Save Changes when you’re done. The next scan evaluates your resources using the newly selected compliance families. You can manually trigger a scan via the UI or API.
Edit Environment from the drop-down menu, and accessing the Compliance tab. Simply check or uncheck the desired compliance family boxes and select Save Changes when you’re done. The next scan evaluates your resources using the newly selected compliance families. You can manually trigger a scan via the UI or API.
Can I create my own family?¶
Yes. You can create your own custom family, and associate the custom family with one or more Fugue-defined or custom rules. Custom families will appear alongside Fugue-defined families in filters and in configuration options throughout Fugue. See Families for instructions.
Can I waive a rule or “ignore” a noncompliant resource?¶
Fugue enables you to waive a rule in an environment for one resource at a time or all affected resources (including resources added in the future). When a rule is waived for a resource, the rule result – PASS or FAIL – is effectively ignored in compliance calculations for that environment. A failed rule doesn’t count against a resource when compliance is calculated.
To learn more about waivers, see Waivers.
If you want to completely disable a rule for all relevant resources and all environments with associated compliance families, see Can I disable a rule for all environments?
Can I disable a rule for all environments?¶
Fugue allows you to disable or enable Fugue rules or custom rules at the organization level. When a rule is disabled, it is not applied to any resource in any environment. When a rule is enabled, it is applied to relevant resources in all environments with an associated family. For instructions and details about how this affects your compliance posture, see Enabling and Disabling Rules.
How do I waive a rule?¶
To waive a custom or out-of-the-box rule, see How to Waive a Rule.
Will changing my compliance standards and saving them automatically trigger a new scan?¶
No, the next scan will still run at its scheduled time. However, you can manually trigger a scan via the UI or API, or change the scan interval using the API.
How can I output a CSV or Excel file of compliance results for my Fugue account?¶
To export compliance data for all environments in a Fugue account, see Export Data.
How are compliance controls and families displayed in the UI?¶
Fugue made changes to how compliance controls and families are displayed in the UI to reflect the “version” of a given compliance family. The format is outlined below:
Compliance v1 |
Compliance v2 |
|---|---|
CIS |
CIS AWS (v1.2.0) |
CIS AWS (v1.3.0) |
|
CIS Google (v1.1.0) |
|
CISAZURE |
CIS Azure (v1.1.0) |
CISCONTROLS |
CIS Controls (v7.1) |
CISCONTROLSAZURE |
CIS Controls (v7.1) |
CIS Docker (v1.2.0) |
|
CSACCM |
CSA CCM (v3.0.1) |
GDPR |
GDPR (v2016) |
GDPRAZURE |
GDPR (v2016) |
HIPAA |
HIPAA (v2013) |
HIPAAAZURE |
HIPAA (v2013) |
ISO27001 |
ISO 27001 (v2013) |
ISO27001AZURE |
ISO 27001 (v2013) |
NIST |
NIST 800-53 (vRev4) |
NISTAZURE |
NIST 800-53 (vRev4) |
PCI |
PCI DSS (v3.2.1) |
PCIAZURE |
PCI DSS (v3.2.1) |
SOC2 |
SOC 2 (v2017) |
SOC2AZURE |
SOC 2 (v2017) |
Drift Detection & Enforcement¶
How do I set or update a baseline?¶
There are several ways to set or update a baseline:
To disable a baseline, see Disabling a Baseline & Drift Detection.
Can I turn off drift detection?¶
You can disable the baseline in order to disable drift detection. You can also suppress drift events at a resource level.
Note that certain resource types do not report drift, by design. See Resource Types That Don’t Report Drift for details.
How do I enable enforcement? (AWS & AWS GovCloud)¶
Before Fugue can enforce your resource configuration, the following steps are required:
Update the IAM role to allow Fugue to modify configuration of the selected resources.
Set a baseline to establish the “known-good” state that drifted resources should be reverted to.
Enable enforcement through Enforcement Settings. There are two ways to access it:
By selecting
 Edit Environment from the Actions drop-down in the top right of the page
Edit Environment from the Actions drop-down in the top right of the pageBy selecting the Disabled or Enabled link below Baseline Enforcement
The Enforcement Settings tab contains a checkbox that allows you to enable or disable baseline enforcement. To enable it, check the box. Then, click “Save changes.” The next scan reflects the changes. You can manually trigger a scan via the UI or API.
You can also enable and disable enforcement through the API.
For more information about enabling enforcement, see Environment Configuration.
How do I disable enforcement? (AWS & AWS GovCloud)¶
You can disable enforcement through the Enforcement Settings tab. There are two ways to access it:
By selecting
 Edit Environment from the Actions drop-down in the top right of the page
Edit Environment from the Actions drop-down in the top right of the pageBy selecting the Disabled or Enabled link below Baseline Enforcement
The Enforcement Settings tab contains a checkbox that allows you to enable or disable baseline enforcement. To disable it, uncheck the box. Then, click “Save changes.” The next scan reflects the changes. You can manually trigger a scan via the UI or API.
You can also enable and disable enforcement through the API.
For more information about disabling enforcement, see Environment Configuration.
How can I change the AWS or AWS GovCloud resources that Fugue enforces?¶
If this is the first time you’re enabling enforcement, see How do I enable enforcement? first.
If you’ve already enabled enforcement, changing the AWS resources Fugue enforces is a two-step process:
Select
 Edit Environment from the Actions drop-down in the top right of the page and select/deselect resources you want to include or exclude from baseline enforcement (“enforce access”). See Service Coverage - AWS & AWS GovCloud for a list of supported resources.
Edit Environment from the Actions drop-down in the top right of the page and select/deselect resources you want to include or exclude from baseline enforcement (“enforce access”). See Service Coverage - AWS & AWS GovCloud for a list of supported resources.Update the IAM policy for the Fugue role. For instructions, see How To: Update the Fugue IAM Role.
The next scan enforces the updated resource types. You can manually trigger a scan via the UI or API.
Warning
After updating the permissions in Fugue, you must update its IAM role in AWS or scans will fail. For instructions, see How To: Update the Fugue IAM Role. You can also reach out to support@fugue.co.
What kind of drift does Fugue enforce?¶
Fugue only supports enforcement of modified resources. It does not delete new resources that have been added or recreate existing resources that have been deleted.
When a resource is enforced, does Fugue simply modify it, or does it destroy the resource and recreate it?¶
Fugue performs mutable updates, which means it changes resource configuration without destroying and recreating the resource itself.
AWS Identity & Access Management (IAM) Permissions¶
What kind of AWS IAM permissions does Fugue need?¶
To scan your account and/or detect drift, Fugue requires certain read-only permissions (“scan access”). To automatically remediate changes to your baseline, Fugue requires certain write permissions (“enforce access”).
See a list of all possible Fugue permissions here.
You can customize which resources Fugue has scan access or enforce access to by ticking the appropriate checkboxes in the Edit Environment Settings dialog. (See note about scan permissions.)
For a quick tutorial on creating the IAM role, see How To: Create a Fugue IAM Role.
SecurityAudit read-only policy¶
When you launch a CloudFormation stack to create the Fugue role, Fugue automatically attaches the AWS-managed SecurityAudit read-only policy. (For details, see Setup, or visit the AWS docs for the Security Auditor job function.)
Note
When you launch a CloudFormation stack to create the role, the SecurityAudit policy attached to the role grants read-only (scan) access to all supported resources. See a list of all possible Fugue permissions here. For more details, see Setup.
Can I give Fugue enforce access (write permissions) without enabling baseline enforcement?¶
Yes, you can grant Fugue read/write permissions for a particular resource without enabling baseline enforcement. This allows you to give Fugue’s IAM role ARN the correct permissions for drift and enforce protection without having to update the role on a later date. See a list of all possible Fugue permissions here.
What permissions are needed for compliance scanning, drift detection, and baseline enforcement?¶
For compliance scanning and drift detection, scan access (read permission) is needed. For Fugue to perform baseline enforcement, scan access and enforce access (write permission) are needed. See a list of all possible Fugue permissions here.
You can find a CloudFormation template with permissions for all supported AWS resource types in AWS IAM Policy Permissions (AWS standard regions only, not GovCloud).
How do I update the Fugue IAM role trust policy?¶
In response to a security event, Fugue may require you to change the trusted entity that can assume the Fugue IAM role. For instructions, see How To: Update the Fugue IAM Role.
What’s the SecurityAudit policy and why is it attached?¶
SecurityAudit is an AWS-managed policy that grants read-only (scan) access to all supported resources. When you launch a CloudFormation stack to create the Fugue role, the policy is automatically attached. Fugue also creates an inline policy for any permissions not covered by the SecurityAudit policy, such as enforcement (write) permissions.
For more details, see Setup, or visit the AWS docs for the Security Auditor job function.
Why does Fugue use inline policies instead of managed policies?¶
A customer-managed policy is a standalone policy that can be attached to multiple principals. An inline policy is embedded in a single principal and cannot be attached to others, so it can’t be used to escalate other principals’ privileges. Additionally, an inline role is deleted when its principal is deleted. For these reasons, Fugue uses inline policies. Learn more in the AWS docs.
Azure Service Principal Role¶
What type of RBAC role does Fugue require to scan my Azure infrastructure?¶
Fugue needs a Reader role in order to scan your Azure resource groups. For details, see Setup - Azure.
Service Coverage¶
What cloud provider services does Fugue support?¶
See our service coverage pages for AWS & AWS GovCloud, Azure & Azure Government, and Google Cloud for a list of currently supported services.
Organization¶
How do I manage users?¶
For instructions on managing users, see User Management.
For information about managing users with RBAC, see Role-Based Access Control (RBAC).
For information about using single sign-on with Fugue, see Single Sign-on (SSO).
For information about using MFA with Fugue, see Multi-Factor Authentication (MFA).
How do I use RBAC to manage users?¶
For information about using RBAC to manage users, see Role-Based Access Control (RBAC).
How do I enable SSO?¶
For information about using single sign-on with Fugue, see Single Sign-on (SSO). To enable SSO, contact support@fugue.co.
How do I enable MFA?¶
For information about using MFA with Fugue, see Multi-Factor Authentication (MFA). To enable MFA, contact support@fugue.co.
Visualizer¶
How can I visualize the resources in my environment?¶
The cloud resource visualizer creates detailed, auto-generated, interactive diagrams of the infrastructure in your environment. To access the visualizer, select the Visualizer link in the header near the top of the page:
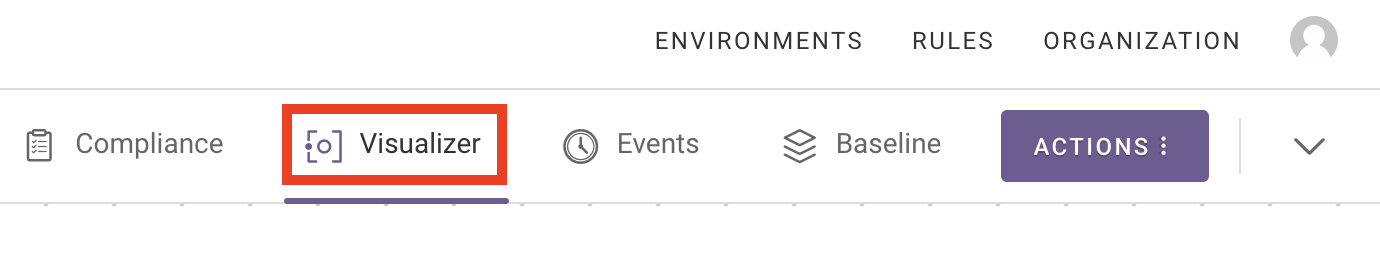
See the visualizer documentation for more information.
What resource types are visualized?¶
For the complete list, see Which Resources Are Visualized? in the visualizer documentation.
What do the characters next to subnet and security group names mean?¶
The two characters next to a subnet name or CIDR block or a security group represent the first two digits of the resource ID. For an example, see Which Resources Are Visualized? in the visualizer documentation.
Which cloud providers are supported?¶
The visualizer supports environments in AWS standard and GovCloud regions, Azure and Azure Government, and Google Cloud.
Does the visualizer support keyboard shortcuts?¶
The visualizer supports the following keyboard shortcuts:
Pan: Arrow keys
Zoom in: Plus
+(equals=)Zoom out: Minus
-(underscore_)Open/close View Options panel: Period
.Center/reset zoom: Double-tap the spacebar
Notifications¶
What if I have a question about notifications?¶
For FAQs about notifications, see Notifications.
Audit Log¶
Does Fugue have audit logging capabilities?¶
Fugue supports audit logging for write actions - such as environment creation/deletion, custom rule creation/deletion, and environment scans - taken by users and API clients. The audit log can be accessed with the Fugue API by accessing the GET audit_log/events/ endpoint. For more information, see the API Reference and API Examples.
Best Practices¶
AWS Regions and Environments¶
Since Fugue allows you to create multiple environments per region, and environments may contain multiple regions, we recommend that you only enable enforcement once per region. Enabling enforcement in the same region multiple times can introduce enforcement conflicts.
In order to determine compliance across an AWS account, it’s a best practice to create environments for all regions in which you’ve configured infrastructure.
For more information about setting up environments, see Setup - AWS & AWS GovCloud and Environment Configuration.
Recommended AWS Resource Types to Scan¶
In order to get the most out of Fugue, you can opt to scan a Fugue-recommended set of resource types when creating an environment. We’ve chosen these resources for the Fugue Recommended Resource Types list because of their high impact on security, and they include security groups, IAM roles, S3 buckets, and more.
See the Fugue-recommended resource types in our Service Coverage - AWS & AWS GovCloud page. Recommended resources appear with an (R).
Avoid Enforcing AWS Auto Scaled Resources¶
Enabling enforcement on auto scaled resources is not recommended. This is because AWS dynamically adjusts auto scaled resource properties when there is a scaling event, but Fugue adjusts the resource properties when they diverge from the baseline, which in turn causes AWS to adjust them again. This creates a cycle of potentially destructive changes to infrastructure and/or increased costs.
For example, if an Auto Scaling group’s desired capacity is set to 2 in the Fugue baseline and enforcement is enabled, but an auto scaling event occurs and AWS launches a third instance, Fugue will set the desired capacity back to 2 on its next scan and cause AWS to terminate the third instance. AWS will then increase the desired capacity again due to the auto scaling event.
Elastic Load Balancers are similarly affected. Because a baseline captures auto scaled instances attached to an ELB, Fugue may remediate the ELB by attempting to reattach terminated instances. This is true even if enforcement is not enabled for the Auto Scaling group.
Likewise, if an auto scaled DynamoDB table has a baseline of 5 provisioned read capacity units but an auto scaling event causes AWS to decrease throughput to 1, Fugue will set it back to 5 on its next scan, and so on.
As a best practice, we recommend that you do not enable enforcement for the following resources:
AutoScaling.AutoScalingGroup
ELB.LoadBalancer
DynamoDB.Table
Enable Multi-Factor Authentication (MFA)¶
It’s a security best practice to enable multi-factor authentication (MFA) where available. To enable MFA for your Fugue organization, see the User Management page and contact support@fugue.co.
Known Issues¶
Maximum of 1,000 SQS Queues¶
Due to a limitation of the AWS API, the maximum number of SQS queues Fugue may scan in an account at once is 1,000. Additionally, the AWS API may not reliably return the same 1,000 queues every scan. As a result, users with more than 1,000 queues will be unable to see them all at once in Fugue, and the precise list of queues displayed will vary.
Notification of Newly Compliant Resources When Transitioning to Fugue Developer¶
Currently, under specific conditions, a Trial user who has enabled notifications and transitions to Developer may receive a notification that certain noncompliant resources are newly compliant. This only occurs if all of the following are true:
The user is a Trial user who transitions to Developer
The user has notifications enabled
The user has enabled compliance families that are unsupported in Developer (that is, any family other than CIS AWS, CIS Azure, and Fugue Best Practices)
The user has resources that are noncompliant with the unsupported compliance families
Additional Resources about Cloud Security¶
For additional resources about cloud security, see Fugue’s blog:
Other¶
What if I have other questions?¶
Reach out to support@fugue.co for assistance.
